this post was submitted on 20 Oct 2024
426 points (98.9% liked)
Piracy: ꜱᴀɪʟ ᴛʜᴇ ʜɪɢʜ ꜱᴇᴀꜱ
54424 readers
1128 users here now
⚓ Dedicated to the discussion of digital piracy, including ethical problems and legal advancements.
Rules • Full Version
1. Posts must be related to the discussion of digital piracy
2. Don't request invites, trade, sell, or self-promote
3. Don't request or link to specific pirated titles, including DMs
4. Don't submit low-quality posts, be entitled, or harass others
Loot, Pillage, & Plunder
📜 c/Piracy Wiki (Community Edition):
💰 Please help cover server costs.
 |
 |
|---|---|
| Ko-fi | Liberapay |
founded 1 year ago
MODERATORS
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments

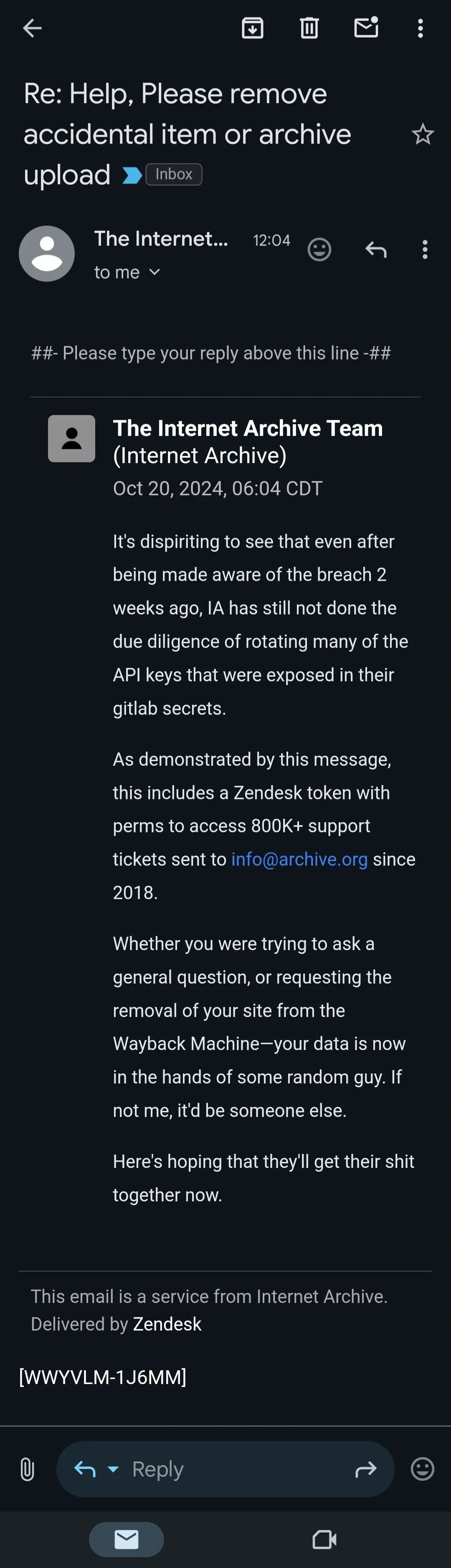
This person could be damaging corporate infrastructure but he goes after internet archive
I mean this person seems to be not doing it maliciously. As they say, if it wasn't them, it would be someone else. Pushing archive to improve their security is great for everyone. As long as this person doesn't do anything actually malicious, they're in the clear as far as I'm concerned.
This guy is outing the archive for terrible security posture by bringing attention to it because they received disclosures and did not fix them.
Don't get shit twisted - he's the hero here. IA fucked up and has been vulnerable to manipulation by any number of corporate or national actors this entire time.
You don't leak a passwords database publicly on the Internet in good faith.
Not necessarily the same hacker.
It's not uncommon for hackers to sell cures for problems they cause. This includes law enforcement, which can have broader goals like promoting their own cybersecurity outfits, even just promoting deoendency on HIBP if it's a fed thing would be useful here, making the joke they left on the page telling people to check out the site itself suspect. The internet archive is a large and beloved outlet for piracy and depaywalling, maybe the security enhancements being billed to them could help the industry bring them to heel a bit. Just speculating.
Are you saying the person who sent the zendesk email is going to try to get IA to hire them for something? I'm not sure I follow...
No I think it's about "context creation" as they call it. Like a protetection racket where payment is made in dependence on certain tools, that is intended to be used later. Good way to popularize leaks themselves
Still not sure what you're talking about.. Is someone going to ask IA for payment related to the zendesk email?
I said it was about fostering dependence on the cybersecurity community. To what end, I do not kniw. But getting people to cloudflare their sites is great for surveillance. Cybersecurity outlets are intensely political and pro west.
Private security contractors have noted that leftists use the internet archive more than anyone. I have been reading their papers about online extremism. Very bad people
Thanks for clarifying.
I'm a vague motherfucker and sometimes I just get the feeling if I try to explain my three-quarters baked understanding of how intelligence works in academia and the tech or culture industry in an overtly benign way, I'm going to be tedious due to my lack of expert knowledge ᕕ( ᐛ )ᕗ like I should learn more first, to avoid being tedious
You sure about that, or are you hypothesizing?
There's never certainty when talking about hackers...
That's verbatim the content of the email and the email hack does not appear to be malicious (unlike the ddos or the password breach)
It's more likely that this is 3 different groups than it is a single group.
If this was genuinely done out of love I could understand but due to the legal battles the internet archive is currently being dragged through, I harbor suspicion of their intent.
If they were really "the hero", they'd follow the bare minimum of responsible disclosure best practices, and allow 90 days between privately alerting them of the issue and going public with it. Two weeks is absurd.
90 days to cycle private tokens/keys?
90 days is just the standard timeframe for responsible disclosure. And normally that's just a baseline with additional time being given if there's genuine communication going on and signs they're addressing the problem.
90 days is standard for "you're code is fucked when someone presses this..."; if the issue is Dave left the keys in the parking lot and someone copied them, two weeks is more than enough time for them to recieve the notice, create a ticket to rotate the keys and a ticket to trigger an investigation (gotta document anytime an org fucks up so it doesn't happen again, right?). Maybe I'm over simplifying it though, I don't know how their org operates.
I agree in general, but
This is exactly why just sticking to the 90 day standard is better. For the supposed security researcher it's a CYA move at worst.
The hackers are mostly not okay. Fucking bootlickers.
I have to say that the way they are advertising "HAVE I BEEN PWNED" makes this look like law enforcement selling cures to problems they create. The owner has that CIA front company type CV. It makes my head shudder uncontrollably. 🐙🌕🤕