Ah of course i was gonna say even with a cgnat they would have some way of identifying the traffic.
aldalire
Thank you. So in a way if the carriers upgrade their infrastructure there would be a decrease in privacy because then it’s a one-to-one correspondence between IP address and customer, but then the customer would have the ability to host servers? The one scenario where the industry dragging their heels on upgrading is actually good for the consumer (in some respects) lol
Adding commas to that number: 4,294,967,296 addresses. More humans that IP address seems like a huge miscalculation in the internet infrastructure
Oh boi i didn’t know ipv6 was this spicy
Ok, i’ll edit my post to include that too, as it seems it’s a more general solution :)
fuck nintendo
fuck nintendo
fuck nintendo
fuck nintendo
How many corn snakes are equivalent to a gf? I have one already.
Pretty neat
Hell yeah bruther, resist capitalism as much as you can
Including the free microplastics from the container? About 3
It has a strawless lid! 10/10 save the turtles

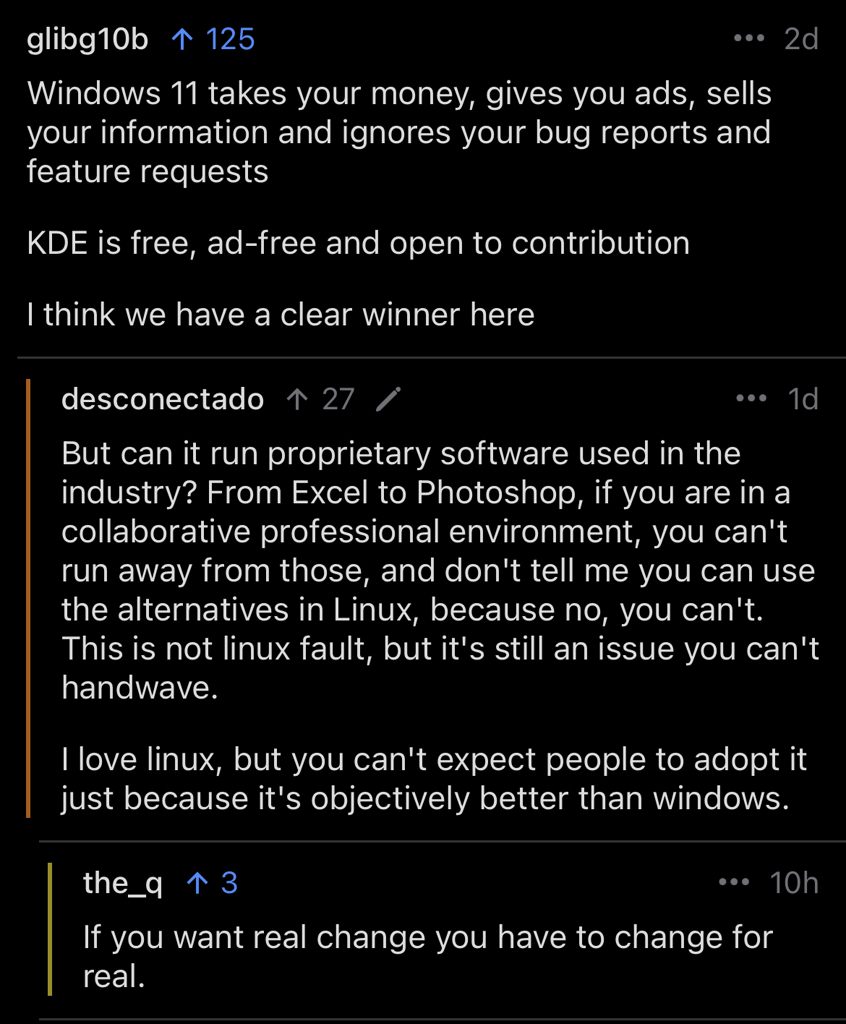



Oh so now i’m depriving my server, a waiter who agreed to be paid hourly, above the legal minimum wage because we’re in California and tips aren’t deducted from his wage, his fair wage by not tipping? Me, a consumer in the restaurant, needs to directly subsidize his wage?
Why?