DO NOT OPEN THE "LEGAL" PAGE
lemmy.world is a victim of an XSS attack right now and the hacker simply injected a JavaScript redirection into the sidebar.
It appears the Lemmy backend does not escape HTML in the main sidebar. Not sure if this is also true for community sidebars.

EDIT:
the exploit is also in the tagline that appears on top of the main feed for status updates, like the following one for SDF Chatter:
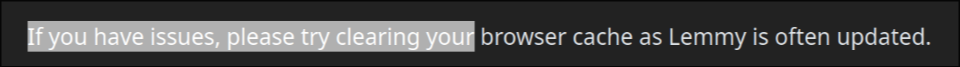
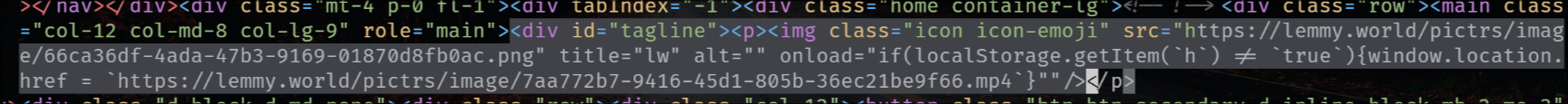
EDIT 2:
The legal information field also has that exploit, so that when you go to the "Legal" page it shows the HTML unescaped, but fortunately (for now) he's using double-quotes.
"legal_information":" 



I don't know too much about lemmy yet, but all of these things (tagline,siudebar and legal info) sound like they should be controlled only by admins, that should be able to add html code anyway (since it their website).
You say it as if it's an intended feature lol, this was an injection attack
If posted text is not properly "escaped" (meaning possible HTML tags and scripts made non-executable), an attacker can post ("inject") javascript in a comment which is then loaded and executed on other people's browsers. It seems that such a method was used to steal log-in cookies from admin's browsers. The attacker then could log in as the admin and proceed to change stuff in other areas of the site.
Edit: someone posted a screenshot of an app displaying the scipt here: https://lemmy.sdf.org/comment/850269 -- the app doesn't execute JS but displays it as text. That might be the safest way to go atm while malicious comments are spreading over the net.
(From that post we also learn about a fix that came almost immediately, so hopefully this issue is being done with as soon as all vulnerable servers have been updated)