this post was submitted on 06 Oct 2024
734 points (90.8% liked)
Technology
59467 readers
4375 users here now
This is a most excellent place for technology news and articles.
Our Rules
- Follow the lemmy.world rules.
- Only tech related content.
- Be excellent to each another!
- Mod approved content bots can post up to 10 articles per day.
- Threads asking for personal tech support may be deleted.
- Politics threads may be removed.
- No memes allowed as posts, OK to post as comments.
- Only approved bots from the list below, to ask if your bot can be added please contact us.
- Check for duplicates before posting, duplicates may be removed
Approved Bots
founded 1 year ago
MODERATORS
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments
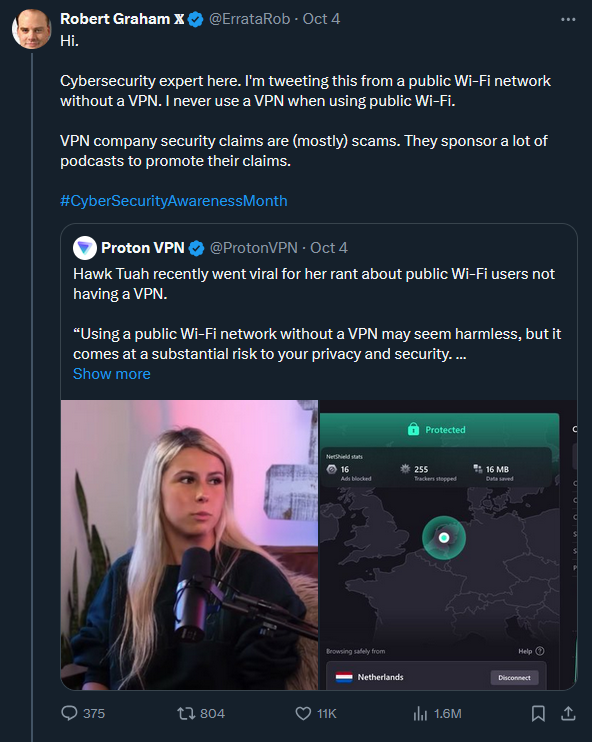
So I'm confused networking stuff has never been my strong suit, is this saying you can still be fucked on public WiFi even if you connect through a VPN?
There are some attacks you are vulnerable to on public WiFi that a VPN can help with.
More generally, whoever is transporting your data knows who you are talking to. If you don’t use a VPN, your ISP and whoever owns the router know what websites you are visiting (although they don’t know the specific content). If you use a VPN, your ISP and router know you are using that VPN, but not what websites you are visiting. Now your VPN knows what websites you are visiting, but they still don’t know what the content is.
I hope that helps.
What about DoH/DoT which comes enabled by default in some browsers I believe? This should "hide" your activity from isp/router as well, shouldn't it?
Yes and no.
Modern HTTPS connections send the URL you are connecting to in the initial hello, so the remote webserver knows what security certificate to use when you connect. A lot of web servers host multiple sites, especially for smaller webpages, and so it doesn't assume that since you connected to that specific webserver, that you're connecting to the site that the webserver is hosting, even if it's only hosting a single site.
This can leak the data to anyone sniffing the traffic.
You can also determine some traffic by IP address, this is for larger web services like Facebook, youtube and other sites of similar size. They load balance groups of IPs for their traffic, all are serving the same data. So if you connect to an IP that's owned by Facebook, for example, then your actions can be easily derived.
Since the connection is still secured by TLS, the content can't be deciphered, but the location you are going to absolutely can.
It really depends on a lot of factors.
Ok, thank you and all the others for explanation.