Selfhosted
A place to share alternatives to popular online services that can be self-hosted without giving up privacy or locking you into a service you don't control.
Rules:
-
Be civil: we're here to support and learn from one another. Insults won't be tolerated. Flame wars are frowned upon.
-
No spam posting.
-
Posts have to be centered around self-hosting. There are other communities for discussing hardware or home computing. If it's not obvious why your post topic revolves around selfhosting, please include details to make it clear.
-
Don't duplicate the full text of your blog or github here. Just post the link for folks to click.
-
Submission headline should match the article title (don’t cherry-pick information from the title to fit your agenda).
-
No trolling.
Resources:
- selfh.st Newsletter and index of selfhosted software and apps
- awesome-selfhosted software
- awesome-sysadmin resources
- Self-Hosted Podcast from Jupiter Broadcasting
Any issues on the community? Report it using the report flag.
Questions? DM the mods!
view the rest of the comments
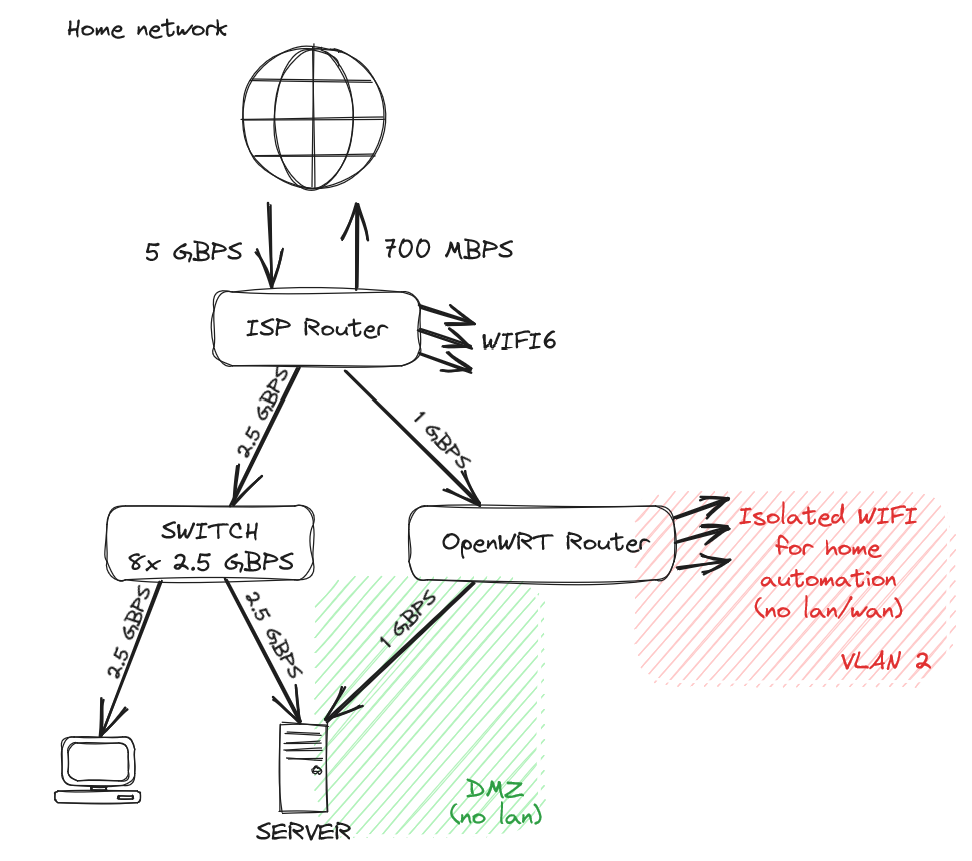
As an FYI: this set up is vulnerable to ARP spoofing. I personally wouldn’t use any ISP-owned routers other than for NAT.
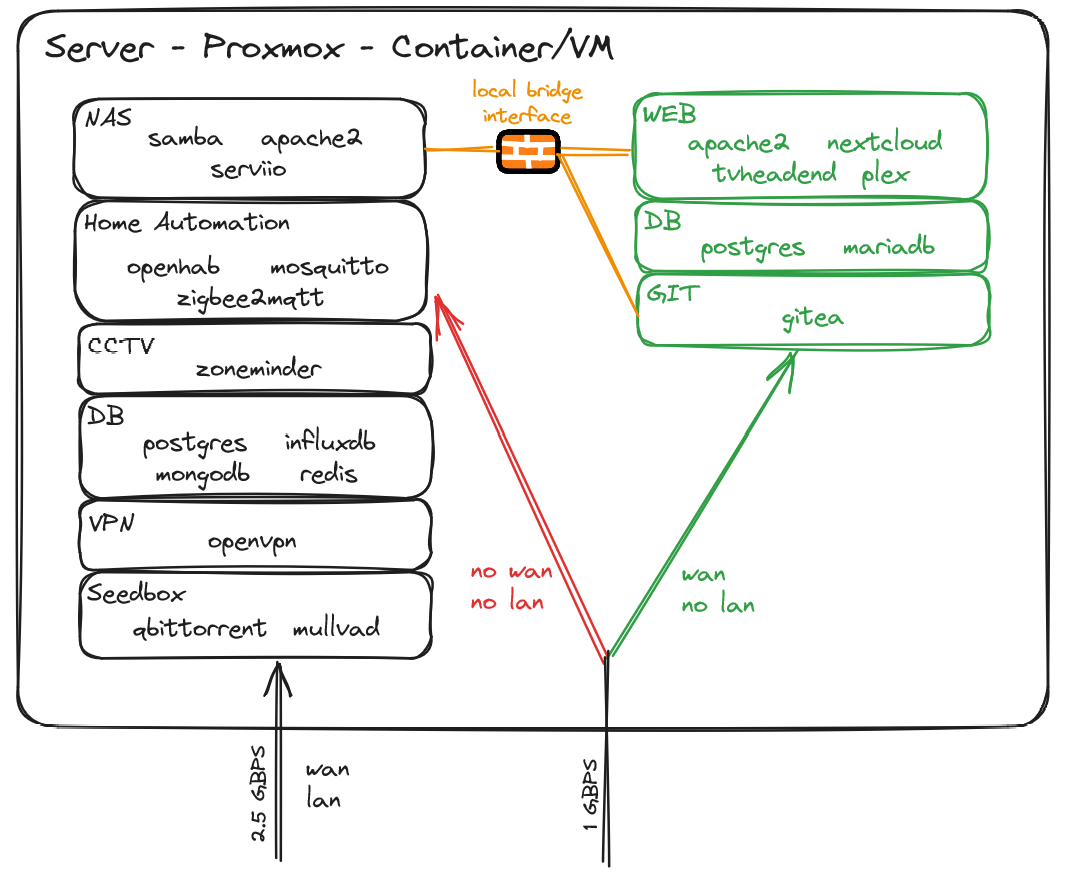
I'm not well versed in ARP spoofing attack and I'll dig around, but assuming the attacker gets access to a "public" VM, its only network adapter is linked to the openwrt router that has 3 separated zones (home lan, home automation, dmz). So I don't think he could have any impact on the lan? No lan traffic is ever going through the openwrt router.
The risk is the ISP Wi-Fi. As long as you’re using WPA with a good long random passkey, the risk is minimal. However, anyone who had access to your Wi-Fi could initiate an ARP spoof (essentially be a man-in-the-middle)
ETA: the ARP table in networking is a cache of which IP is associated with which MAC Address. By “poisoning” or “spoofing” this table in the router and/or clients, a bad actor can see all unencrypted traffic.
How would you change his setup to prevent ARP attacks? More network segmentation (clients and servers on separate VLANs) or does OPNsense additional protections I should look into?
Well, to be honest if someone has access to my Wi-Fi, I'd consider that I've already lost. As soon as you're on my lan, you have access to a ton of things. With this setup I'm not trying to protect against local attacks, but from breaches coming from the internet